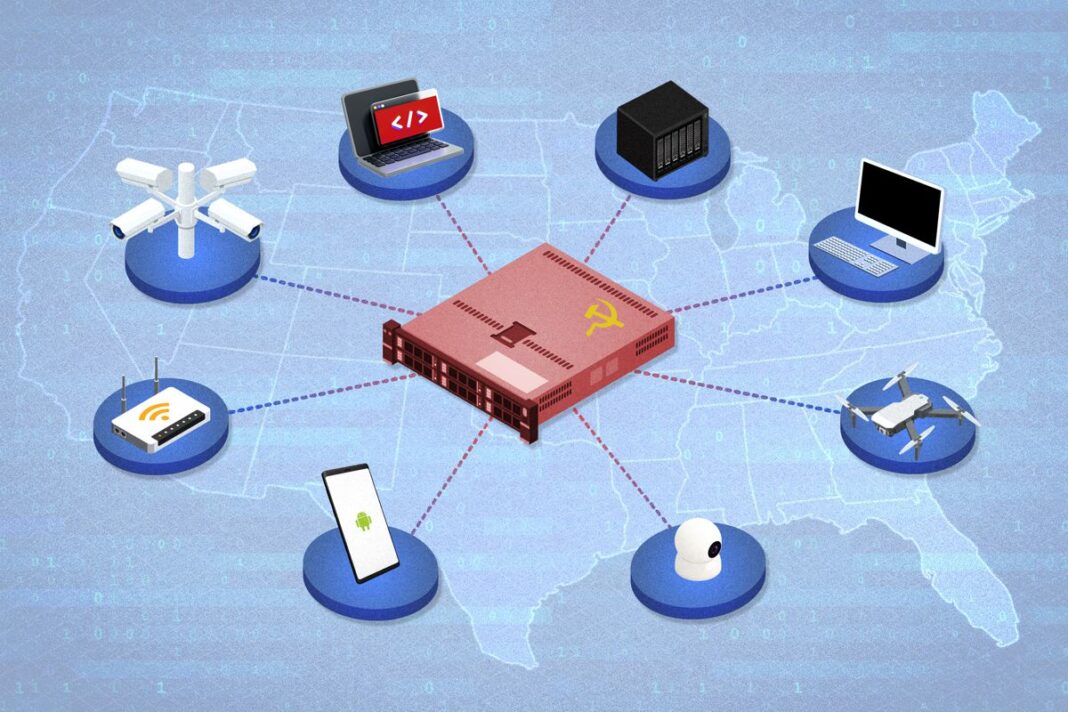
Chinese-made devices have been repeatedly exploited as part of a Beijing-backed effort to undermine and destabilize the United States.
News Analysis
For more than a decade, cybersecurity experts across the government and private sectors have sounded the alarm about the increasing risks posed by technology products manufactured in China.
From preinstalled malware on consumer devices to sabotage operations in critical infrastructure, the United States’ longstanding dependency on Chinese-made devices has been repeatedly exploited as part of a state-backed effort by China’s ruling communist regime to undermine the strategic interests and national security of the United States.
While not every Chinese-made device poses such a risk, the growing catalog of cyberattacks exploiting Chinese hardware underscores the need for vigilance when purchasing or using such products, and suggests the U.S. government may need to do more to curb its reliance on China for a broad array of devices.
Here’s a look at some of the most egregious documented uses of Chinese devices in cyberattacks from the last decade.
Chinese Malware Preinstalled on US Government-Funded Phones
Sending Americans’ most sensitive personal information directly to China probably wasn’t what the Federal Communications Commission had in mind when it decided to subsidize affordable mobile phones for millions of low-income Americans.
That’s exactly what happened, however.
Beginning in 2015, a wide range of budget Android phones manufactured by American company BLU in China were systematically preloaded with malware by suspected Chinese state-backed actors.
Those phones were found by cybersecurity company Kryptowire to have been preloaded with malicious software by the Shanghai Adups Technology Company, an opaque IT services company established in China in 2012, with which BLU had contracted to provide service updates for its devices.
The Adups malware operated at the most foundational level of the phones, including in the wireless update and settings apps, meaning that the malware could not be removed without rendering the phones unusable.
For years, Adups collected granular location data, contact lists, logs for calls and texts, and even the full contents of texts from Americans’ phones. Some of the phones even allowed remote actors believed to be based in China to take screenshots or otherwise seize control of the devices.
To make matters worse, all that data were encrypted and sent back to a server in China, where Chinese Communist Party (CCP) law mandates that information is a national resource, effectively transferring Americans’ most personal data directly to the regime.
The malign activity was able to bypass detection for some time because the malware was embedded in the software of the phone and therefore automatically whitelisted by most malware detection tools, which were programmed to assume that a product’s rudimentary software and firmware would not be malicious.
It’s still unclear just how many Americans were caught up in the operation. Adups claimed on its website in 2016 to have a worldwide presence with more than 700 million active users, and that it also produced firmware integrated into mobile phones, semiconductors, wearable devices, cars, and televisions.